Part 1: Intro to Threat Hunting with Powershell Empire, Windows event logs, and Graylog | HoldMyBeer

Practical Threat Intelligence and Data-Driven Threat Hunting: A hands-on guide to threat hunting with the ATT&CK™ Framework and open source tools: Costa-Gazcón, Valentina: 9781838556372: Amazon.com: Books




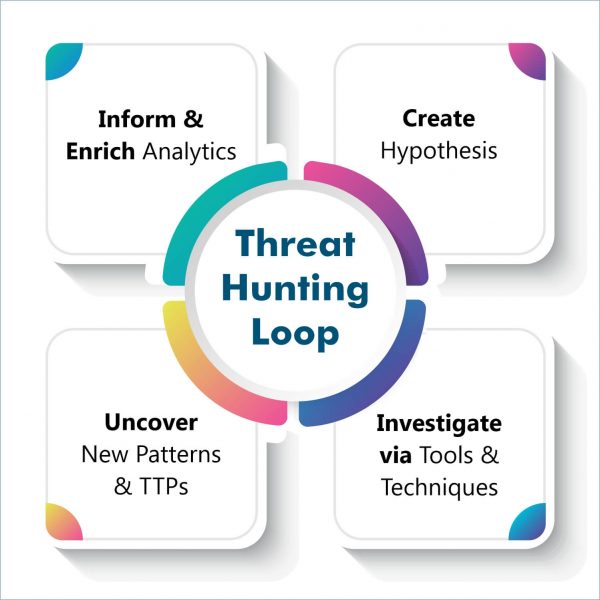
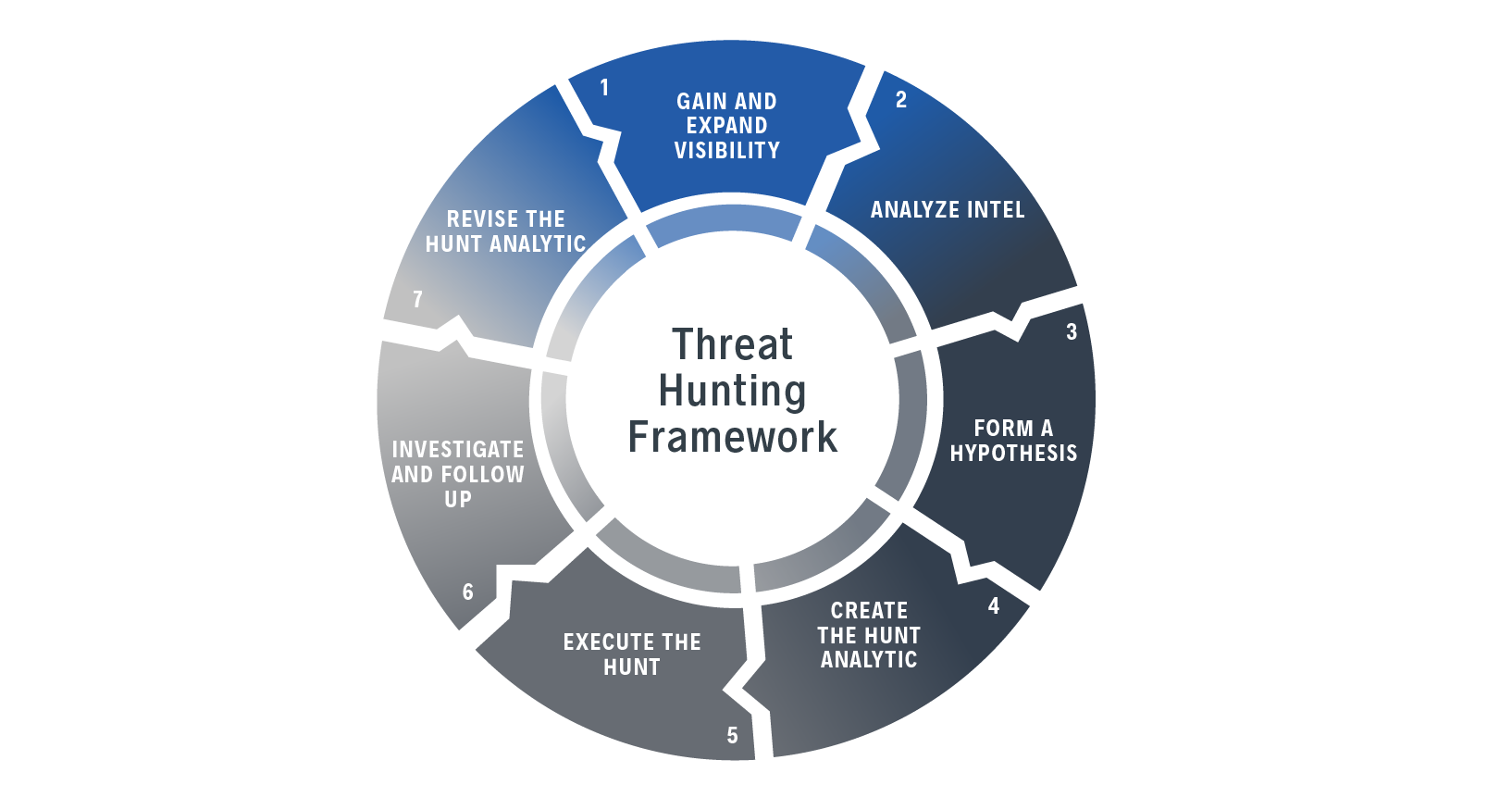
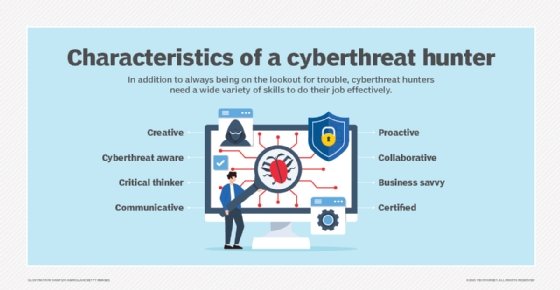

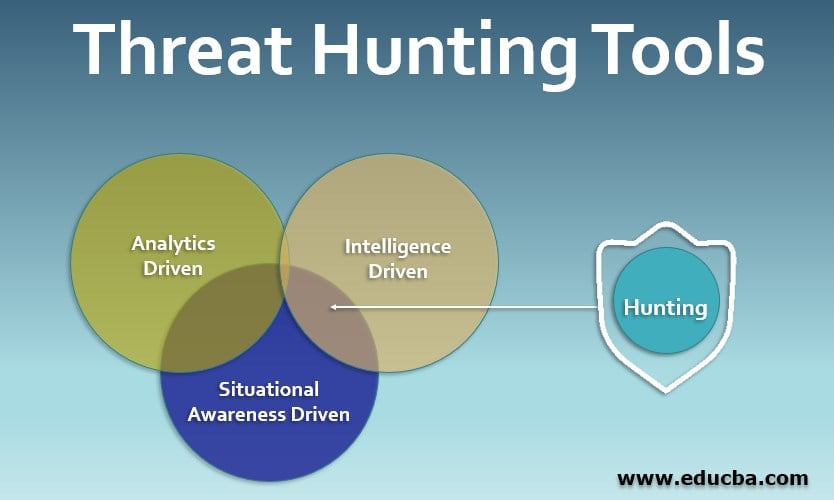

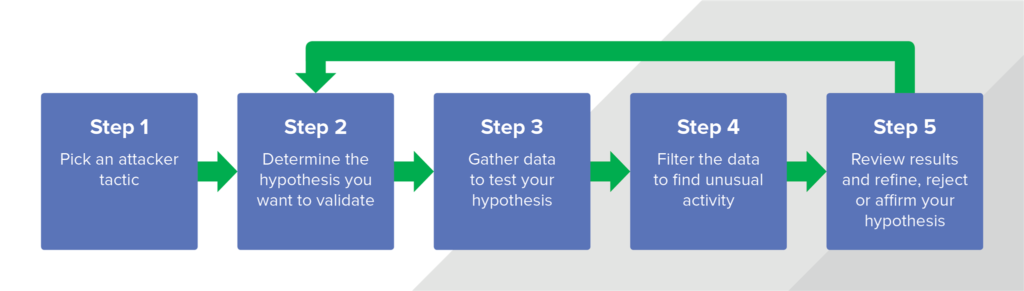
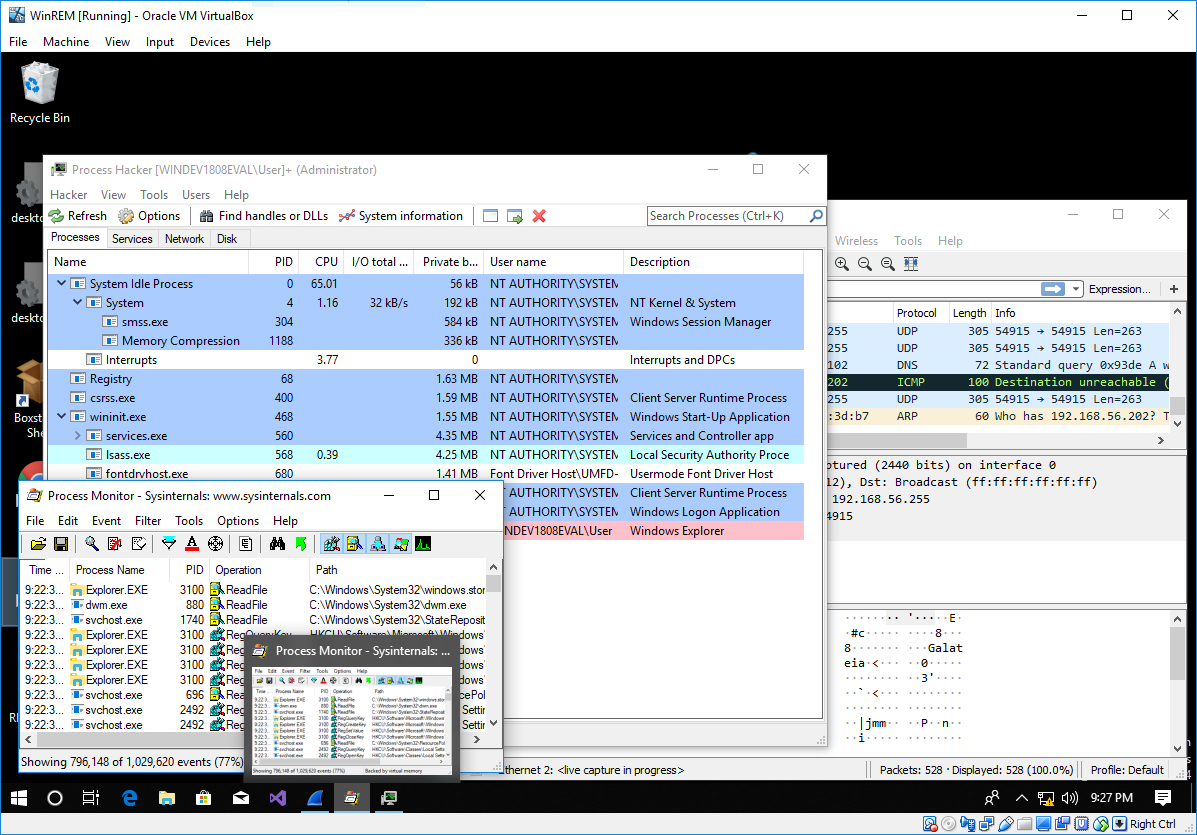
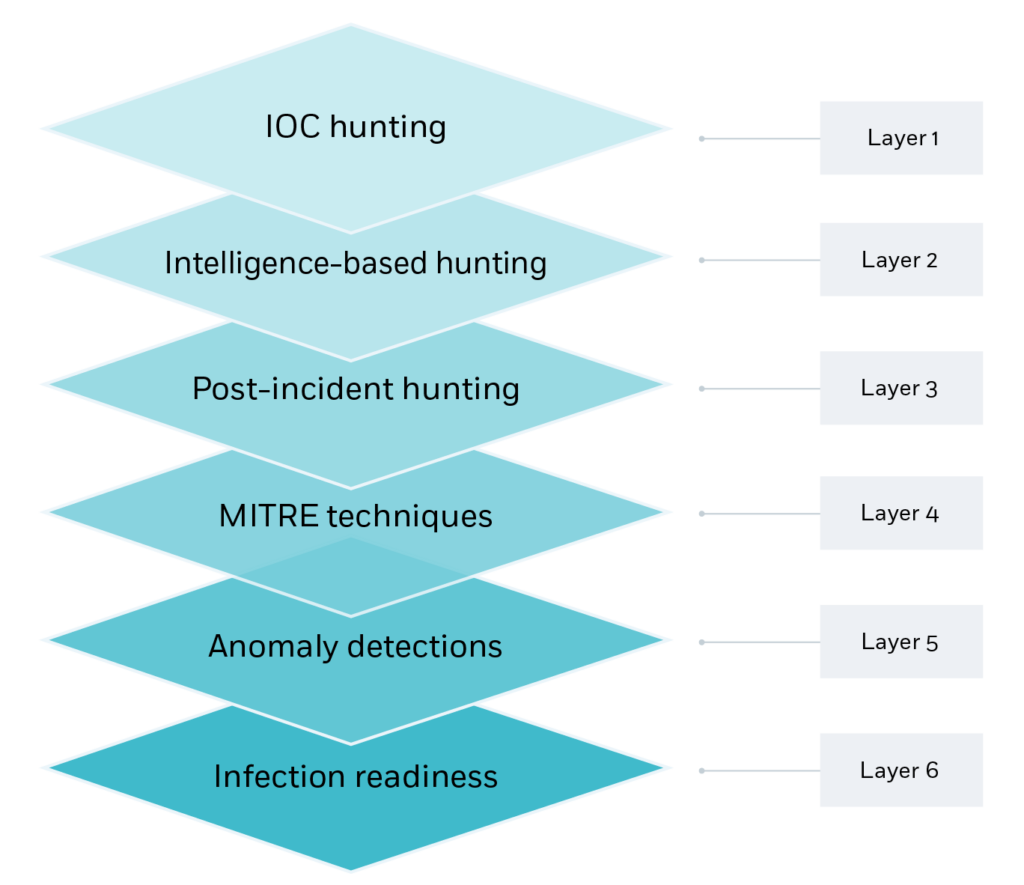

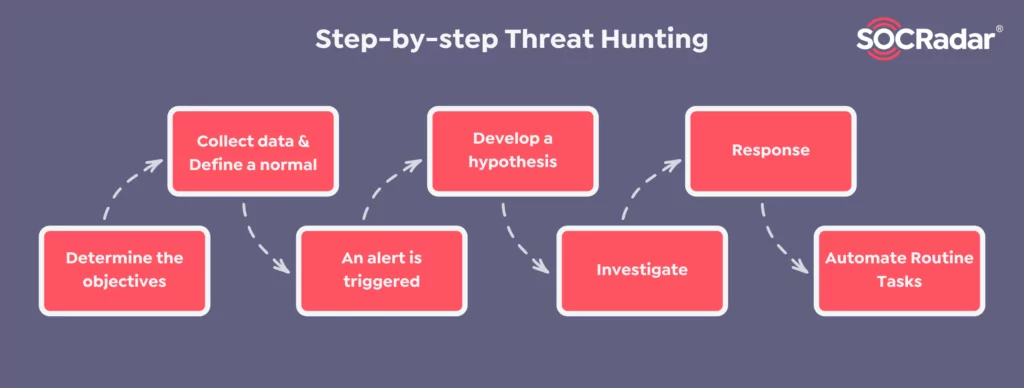


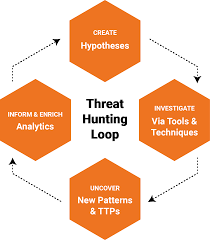
![What is Cyber Threat Hunting? [Proactive Guide] - CrowdStrike What is Cyber Threat Hunting? [Proactive Guide] - CrowdStrike](https://www.crowdstrike.com/wp-content/uploads/2019/06/where-does-threat-hunting-fit-graphic.png)

![What is Cyber Threat Hunting? [Proactive Guide] - CrowdStrike What is Cyber Threat Hunting? [Proactive Guide] - CrowdStrike](https://www.crowdstrike.com/wp-content/uploads/2019/06/what-required-for-threat-hunting-300x168.png)

